Threat Intelligence Validation
Threat intelligence is only valuable when it's relevant. vulnix0 translates global threat data into a prioritized, actionable roadmap for your defense. We don't just report on a trending CVE; we confirm if it's an immediate threat to *your* systems.
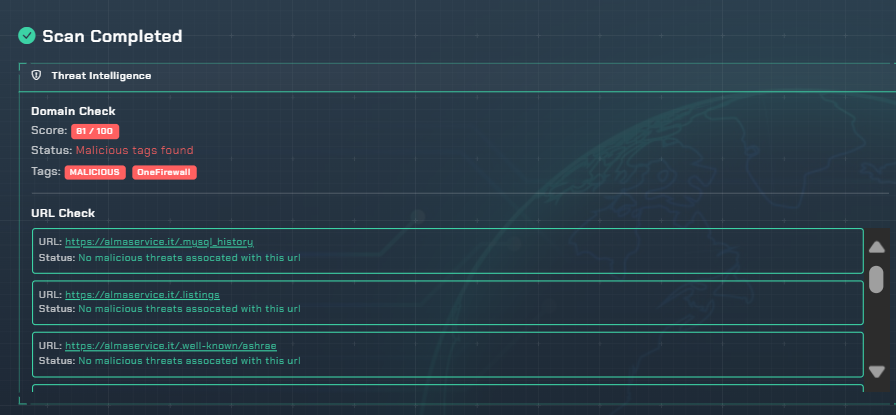
From Noise to Actionable Intelligence
Stop chasing theoretical threats and focus on confirmed exposures.
The Challenge: Intelligence Overload
Security teams are inundated with thousands of generic CVEs, IOCs, and threat reports. This volume of uncontextualized data leads to alert fatigue, desensitizes analysts, and buries critical threats in noise, making effective prioritization impossible.
Our Solution: Attack Surface Correlation
vulnix0 bridges the gap by continuously correlating external threat intelligence with your real-time asset inventory. We instantly determine if a vulnerable technology is present and if a targeted port is exposed, transforming abstract warnings into concrete, validated risks demanding immediate attention.
Key Capabilities
CVE-to-Asset Correlation
When a new CVE is published, vulnix0 instantly cross-references it against your fingerprinted technology stack, immediately identifying every vulnerable asset in your environment.
Live IOC Validation
Continuously validate Indicators of Compromise (malicious IPs, domains) against your live infrastructure, providing real-time alerts on active threats targeting your perimeter.
Context-Driven Prioritization
Threats are prioritized by their real-world context: the asset's public exposure, its business criticality, and active exploitation in the wild—not just a generic CVSS score.
Multi-Source Intelligence Aggregation
We aggregate and normalize data from leading commercial feeds, open-source intelligence (OSINT), and dark web chatter, providing a comprehensive view of the threat landscape as it pertains to you.