Discover Your Complete Attack Surface
It’s the forgotten subdomain or the unmanaged server that leads to a breach.
We map your entire external footprint from an attacker's perspective, so you see what they see.
You Can't Protect What You Can't See
In today's complex cloud environments, manually tracking every website, server, and API is impossible. This "shadow IT" creates dangerous blind spots that attackers love to exploit. Our platform automates the discovery process, giving you a continuously updated inventory of every asset connected to your organization.
Eliminate Security Blind Spots
Find forgotten subdomains, exposed development servers, and third-party services you didn't know you were using.
Gain Continuous Visibility
Your attack surface is always changing. We monitor it constantly, alerting you to new assets the moment they appear online.
A Complete Picture of Your External Risk
Our discovery engine catalogues everything from your network services to the technologies you run.
Subdomain & Host Discovery
We uncover all associated subdomains and virtual hosts, finding legacy applications, APIs, and forgotten marketing sites.
Open Port & Service Scanning
Our scanner identifies all open network ports and the services running on them, from web servers to databases and remote access protocols.
Technology Fingerprinting
We identify the web frameworks, server software, and analytics tools your sites are built on, giving you a complete technology inventory.
DNS & WHOIS Intelligence
We map out your domain's infrastructure, analyzing nameservers, mail servers, and domain registration data for security insights.
TLS/SSL Security Health
We analyze your TLS certificates and server configurations for weak ciphers, expired certificates, and other common misconfigurations.
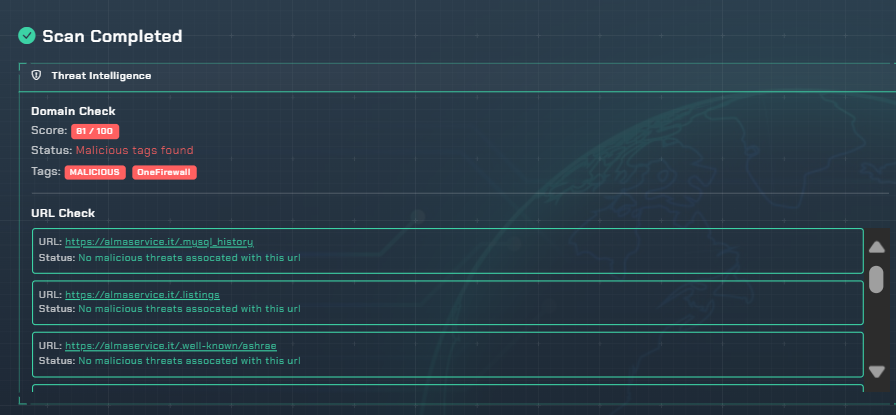
Domain Reputation Check
We check if your domain or any of its subdomains have been flagged for malicious activity, protecting your brand from being blacklisted.
Ready to See Your Full Attack Surface?
Your free discovery scan is just a click away. Map your external assets and identify your security blind spots in minutes.
Start My Discovery Scan