Network Port Scanning
This functionality executes a systematic scan of designated network assets. The primary objective is to
detect open ports, enumerate the services operating on them, and identify potential configuration weaknesses.
The Importance of Port Scanning
An open network port represents a potential vector for unauthorized access. Unmonitored ports can expose services with known vulnerabilities, creating risks such as data exfiltration, malware deployment, or system compromise. Regular port scanning is a foundational component of a robust security strategy.
Attack Surface Minimization
The identification and closure of non-essential ports directly reduces the number of potential entry points for malicious actors.
Comprehensive Asset Visibility
Maintain an accurate inventory of services exposed to the public internet. This helps in detecting unsanctioned or legacy applications.
Data Points and Analysis
The scanning engine generates structured, actionable data to facilitate perimeter security hardening.
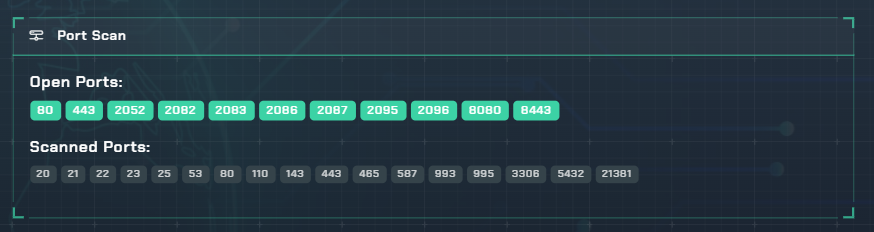
Port Enumeration
Generates a comprehensive list of all open TCP and UDP ports detected on the target assets that are accessible from an external perspective.
Service and Version Identification
The system captures service banners to identify the software and version number operating on each open port, which is crucial for identifying outdated software.
CVE Cross-Referencing
Detected service and version information is automatically correlated against an extensive database of Common Vulnerabilities and Exposures (CVEs).
Firewall Configuration Auditing
Scan outputs can be utilized to validate that firewall rule sets are correctly implemented and are effectively blocking unintended network traffic.
Temporal Change Analysis
The platform maintains a historical log of scan results, enabling the tracking of changes in port status over time to identify modifications to the network perimeter.
Standardized Reporting
Generates detailed reports that include risk categorization, remediation suggestions, and supporting data to enable security teams to efficiently address issues.
Initiate Perimeter Security Analysis
Proactively assess your network's external posture. Begin scanning with the vulnix0 platform to obtain a comprehensive view of your digital attack surface.
Execute Initial Scan