Think Like an Attacker. At Scale.
Standard scanners find vulnerabilities. We find breach paths. vulnix0's Offensive Security Assessments replicate the methods of a human attacker, chaining together weaknesses to discover the complex scenarios that truly threaten your business.
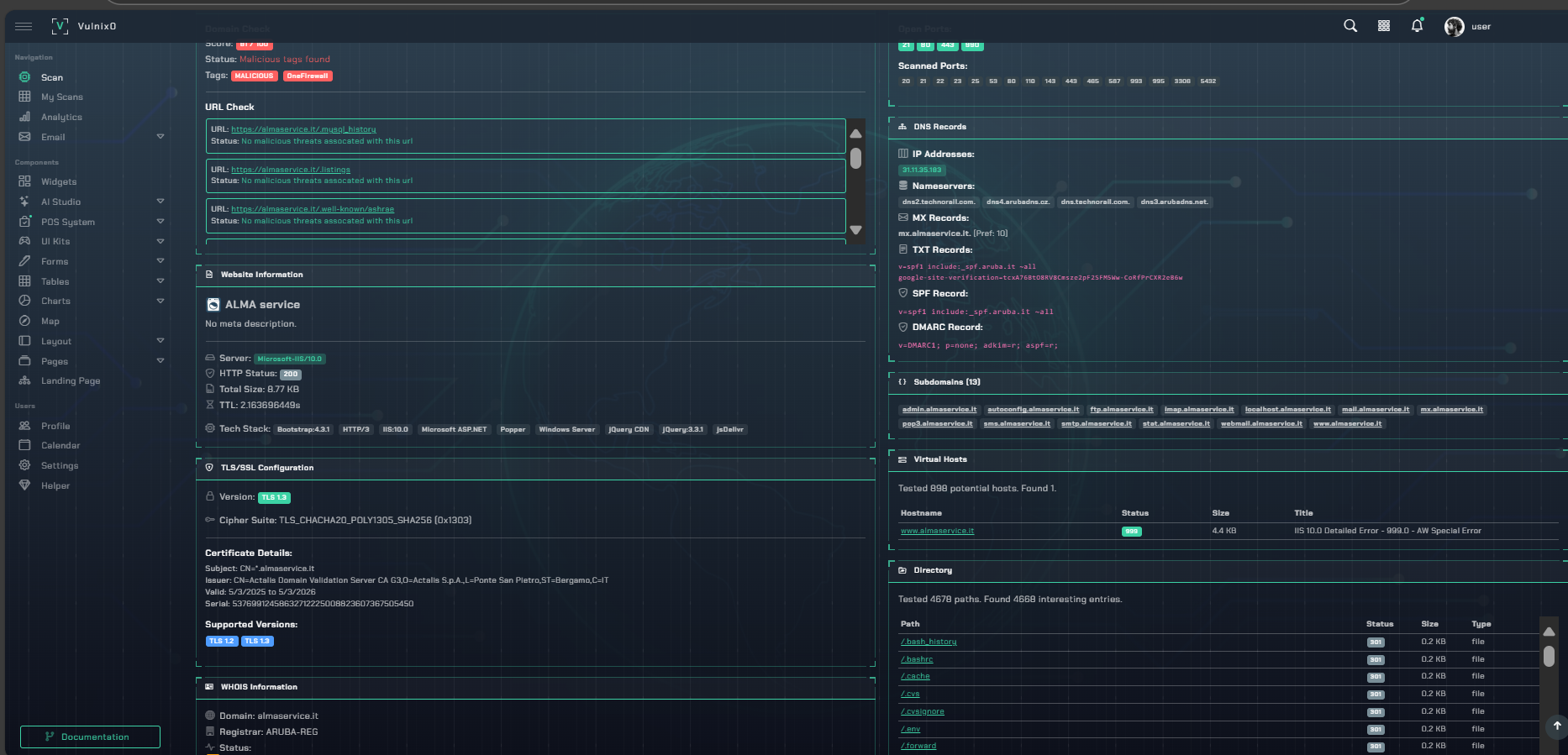
Automation with an Adversarial Mindset
Our advantage comes from fusing machine speed with human creativity.
The Power of Automation
We achieve comprehensive coverage of your entire attack surface at a scale and speed impossible for manual teams, continuously mapping assets and identifying initial weaknesses.
The Logic of a Red Team
Our engine thinks in attack chains. It correlates seemingly low-risk issues to uncover the exact sequence of steps an attacker would take to achieve their objective, from foothold to impact.
What We Uncover
Business Logic Flaws
Exploit flaws in your application's core functions—like payment processing or user authorization—that automated tools are structurally blind to.
Realistic Threat Scenarios
Simulate credible attacks, from data exfiltration routes to the initial access vectors used by ransomware groups, to test your real-world defenses.
Critical Attack Path Analysis
We visualize how an attacker moves from a minor external flaw to a critical internal asset, showing you the exact chain of events to break.
Executive Risk Reporting
Translate technical vulnerabilities into quantifiable business risk. Our reports focus on financial and reputational impact to enable informed decisions.