Asset Discovery & Reconnaissance
Reconnaissance is the foundation of every successful attack. vulnix0 automates this critical phase for your defense, continuously mapping your entire external digital footprint. We provide the same deep intelligence on your perimeter that an advanced adversary would seek, enabling you to identify and secure potential attack vectors before they do.
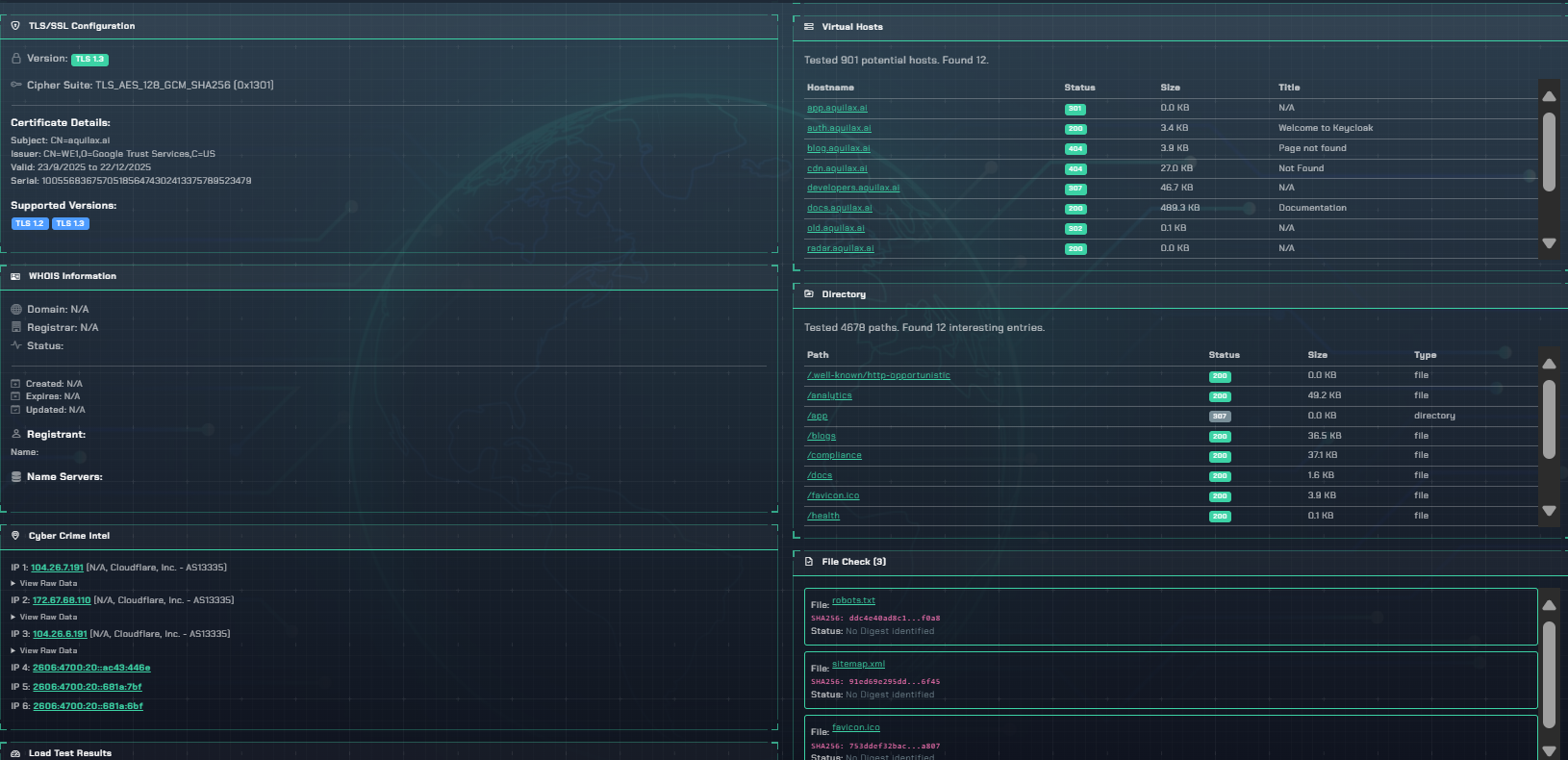
The Reconnaissance dashboard centralizes asset intelligence for immediate analysis and action.
Comprehensive External Reconnaissance
Multi-Vector Subdomain Enumeration
Our multi-vector approach uncovers not just public-facing subdomains but also forgotten development, staging, and API endpoints. These often unpatched assets are prime targets for attackers.
api-v1.your-domain.com
dev-jenkins.your-domain.com
backup.your-domain.com
old-portal.your-domain.com
Port Scanning & Service Fingerprinting
We identify all open ports and, more importantly, fingerprint the services and their versions. This contextual data is crucial for pinpointing exploitable software and outdated systems.
In-Depth DNS Interrogation
Your DNS records are a public roadmap to your infrastructure. We meticulously analyze them to map server relationships and validate critical security policies to prevent email spoofing and other threats.
- Analyzed Records: A, AAAA, CNAME, MX, TXT, SPF, DMARC, DKIM
Technology Stack Fingerprinting
Understanding your technology stack is key to threat modeling. We identify web servers, frameworks, CMS, and third-party libraries, enabling you to track vulnerabilities specific to your software supply chain.
Security Posture Analysis
Discovery without analysis is just noise. We automatically assess the security hygiene of each asset, checking for common misconfigurations and policy violations.
- Validating TLS/SSL certificate chains and cipher strength.
- Auditing for essential security headers (HSTS, CSP, etc.).
- Verifying correct implementation of email security policies.